| << Chapter < Page | Chapter >> Page > |
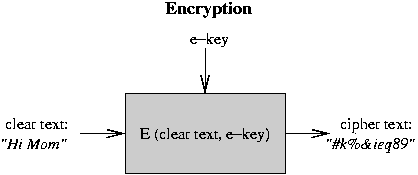
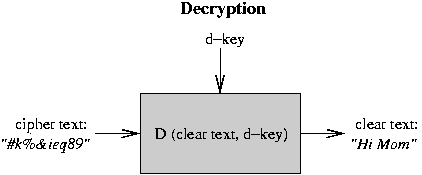
All of this only works under three conditions:
Public key encryption: new mechanism for encryption where knowing the encryption key does not help you to find decryption key, orvice versa.
Safe mail:
It is a nice scheme because the user only has to remember one key, and all senders can use the same key. However, how doesreceiver know for sure who it is getting mail from?
Positive identification: can also use public keys to certify identity:
This is really even better than signatures: harder to forge, and can change if compromised. Note that this idea was developed by anundergraduate (Loren Kohnfelder) in 1978 as part of his undergraduate thesis (at MIT).
These two forms of encryption can be combined together. To identify sender in secure mail, encrypt first with your privatekey, then with receiver's public key. The encryption/decryption functions to send from B to A are:

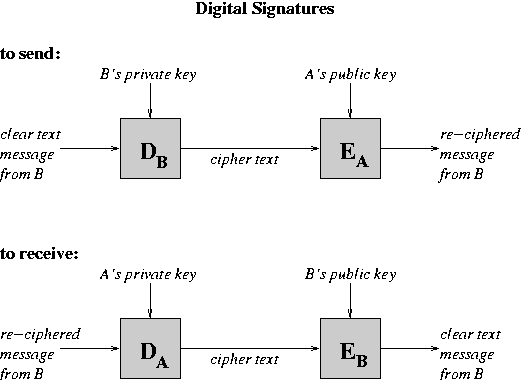
Encryption appears to be a great way to thwart listeners. It does not help with Trojan Horses, though.
Old federal Data Encryption Standard (DES). Is not public-key based, but has been implemented efficiently and appears to berelatively safe.
New Advanced Encryption Standard (AES), called Ryndal.
General problem: how do we know that an encryption mechanism is safe? It is extremely hard to prove. This is a hot topic forresearch: theorists are trying to find provably hard problems, and use them for proving safety of encryption.
Summary of Protection: very hard, but is increasingly important as things like electronic funds transfer become more andmore prevalent.
We would like to thank Prof. Barton Miller for sharing as well as for his valued advice

Notification Switch
Would you like to follow the 'Operating systems' conversation and receive update notifications?