| << Chapter < Page | Chapter >> Page > |
Relying solely upon X509-based PKI models for Grid security suffers from numerous problems. Firstly, users must acquire and manage their own X509 digital certificates often having to convert them to different Grid-oriented formats using specialized software, often far removed from their own domain of expertise. Secondly, X509-based PKI security as used to access resources such as the UK e-Science National Grid Service (NGS – www.ngs.ac.uk) is based on associating a local account on an NGS cluster for a user identified by their DN, to “do stuff” without limiting (authorizing) what this stuff actually is! For security considerations, this is obviously a major issue for many domains. Thirdly, a centralized CA model has issues with supporting longer term identity management. Thus if an individual leaves the organization they are associated with, they probably will still be in possession of their X509 digital certificate. A better model is to support decentralized authentication. In the UK this has been supported through adoption and roll-out of the Internet2 Shibboleth technologies to support devolved (federated) access management (www.ukfederation.org.uk).
The core of Shibboleth is a trust relationship between institutions within a federation, where each institute in the federation is expected (trusted) to authenticate their users properly. The architecture of Shibboleth defines several entities which are necessary to achieve this seamless integration of separate collaborating institutional authentication systems. The main components of Shibboleth consist of Identity Providers (IdPs); a Where-Are-You-From (WAYF) service, and one or more Service Providers (SP). The IdP is typically the users’ home institution and is responsible for authenticating the end users at their institution. Each institution will have their own local systems for authenticating their users, e.g. LDAP or other mechanisms. The WAYF service is generally run by the federation that the institutions are subscribed to. It typically presents a dropdown list to the user that contains all the participating institutions (or projects) that are subscribed to within the federation. Users choose their home institution from this list and are then redirected to the home institution (IdP). The SP provides services or resources for the federation that the end user wishes to access.
A typical scenario of this process is shown in Figure 1, where a user types in the URL of the service or Grid portal (SP) they wish to access.
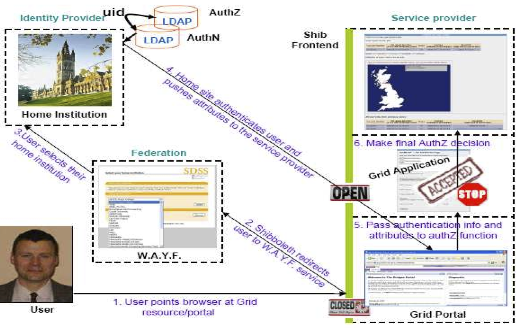
In this model, if the SP is protected by Shibboleth, the user will be redirected to the WAYF service where they select their home institution. Once redirected to their IdP they will provide the username and password they would normally use for authentication at their home institution. Once successfully authenticated, the user will be automatically redirected to the SP they are trying to access. At the same time, the security attributes (privileges) of this user will also be passed to the SP in a secure manner for further authorization from either the IdP or one or more known attribute authorities (AA). What attributes will be released by an institutional IdP or AA and what attributes will be accepted by a given SP needs to be configurable however and targeted towards the needs of particular virtual organizations. It is important that all of this is transparent to the end users (who simply log-in to their home site).

Notification Switch
Would you like to follow the 'Research in a connected world' conversation and receive update notifications?