-
Home
- Operating systems
- Lecture notes
- Memory management
Static relocation with protection keys (IBM S/360
approach):
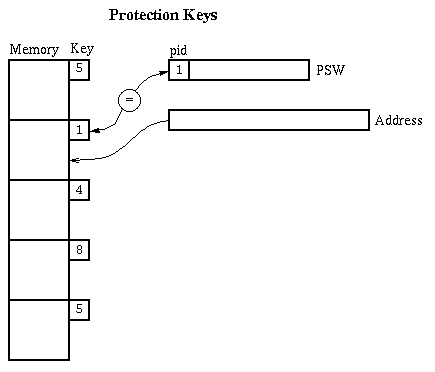
- Protection Key = a small integer stored with each chunk of memory.
The chunks are likely to be 1k-4k bytes.
- Keep an extra hardware register to identify the current process.
This is called the process id, or PID. 0 is reserved for the operating system'sprocess id.
- On every memory reference, check the PID of the current process
against the key of the memory chunk being accessed. PID 0 is allowed to touchanything, but any other mismatch results in an error trap.
- Additional control: who is allowed to set the PID? How does OS
regain control once it has given it up?
- This is the scheme used for the IBM S/360 family. It is safe but
inconvenient:
- Programs have to be
relocated before loading. In some systems (e.g. MPS) this requires completerelinking. Expensive.
- Cannot share information between two
processes very easily
- Cannot swap a process out to secondary
storage and bring it back to a different location
Dynamic memory relocation: instead of changing the
addresses of a program before it is loaded, we change the address dynamicallyduring every reference.
- Under dynamic relocation, each program-generated address (called a
logical or virtual address) is translated in hardware to a physical, or realaddress. This happens as part of each memory reference.
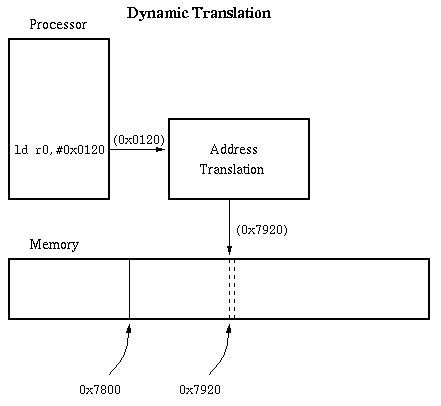
- Show how dynamic relocation leads to two views of memory, called
address spaces. With static relocation we force the views to coincide so thatthere can be several levels of mapping.
Base and bounds, segmentation
Base&bounds relocation:
- Two hardware registers: base address for process, bounds register
that indicates the last valid address the process may generate.
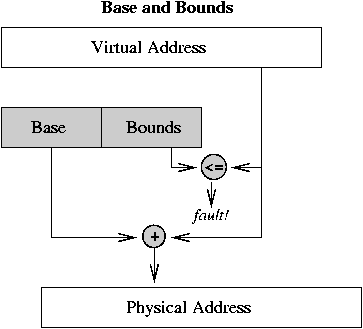
Each process must be allocated contiguously in real
memory.
- On each memory reference, the virtual address is compared to the
bounds register, then added to the base register. A bounds violation results inan error trap.
- Each process appears to have a completely private memory of size
equal to the bounds register plus 1. Processes are protected from each other. Noaddress relocation is necessary when a process is loaded.
- Typically, the OS runs with relocation turned off, and there are
special instructions to branch to and from the OS while at the same time turningrelocation on and off. Modification of the base and bounds registers must also
be controlled.
- Base&bounds is cheap -- only 2 registers -- and fast -- the
add and compare can be done in parallel.
- Explain how swapping can work.
- Examples: CRAY-1.
Problem with base&bound relocation:
- Only one segment. How can two processes share code while keeping
private data areas (e.g. shared editor)? Draw a picture to show that it cannotbe done safely with a single-segment scheme.
Multiple segments.
- Permit process to be split between several areas of memory. Each
area is called a segment and contains a collection of logically-relatedinformation, e.g. code or data for a module.
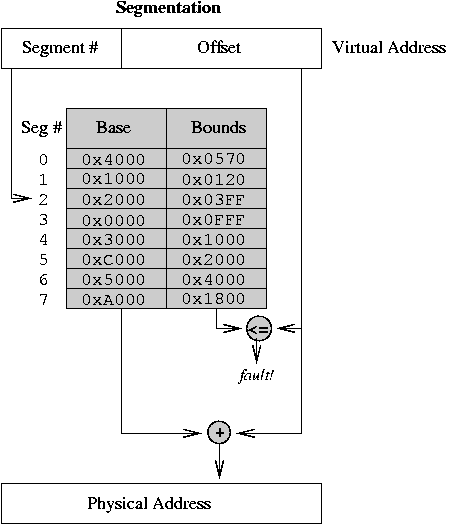
- Use a separate base and bound for each segment, and also add a
protection bit (read/write).
- Each memory reference indicates a segment and offset in one or
more of three ways:
- Top bits of
address select segment, low bits the offset. This is the most common, and thebest.
- Or, segment is selected implicitly by the operation being
performed (e.g. code vs. data, stack vs. data).
- Or, segment is
selected by fields in the instruction (as in Intel x86 prefixes).
Source:
OpenStax, Operating systems. OpenStax CNX. Aug 13, 2009 Download for free at http://cnx.org/content/col10785/1.2
Google Play and the Google Play logo are trademarks of Google Inc.




