| << Chapter < Page | Chapter >> Page > |
Access Lists: with each file, indicate which users are allowed to perform which operations.
Capabilities: with each user, indicate which files may be accessed, and in what ways.
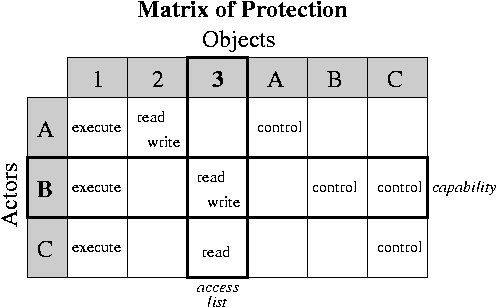
Are the following things access-based or capability-based protection schemes?
Some part of the system must be responsible for enforcing access controls and protecting the authorization and identificationinformation.
The problem addressed by the security system is how are information and resources protected from people. Issues include the contentsof data files which are a privacy issue, and the use of resources, which is an accounting issue. Security must pervade the system, or the system is insecure,but the file system is a particularly good place to discuss security because its protection mechanisms are visible, and the things it protects are very concrete(for a computer system).
We're talking about some interesting stuff when we talk about security. For certain people who like puzzles, finding loopholes insecurity systems and understanding them to the point of breaking them is a challenge. I understand the lure of this. Remember, however, that everyone usingthese machines is a student like yourself who deserves the same respect that you do. Breaking into another person's files is like breaking into their home, andshould not be taken lightly either by those breaking in, or those who catch them. Uninvited intrusions should be dealt with harshly (for example, it's afelony to break into a machine that stores medical records). If you really want to play around with UNIX(R) security, get yourself a linux box and play to yourheart's content; don't break into someone's account here and start deleting files.

Notification Switch
Would you like to follow the 'Operating systems' conversation and receive update notifications?